Forwarded Headers
On this page
TheX-Forwarded-* headers presented to Authelia must be from trusted sources. As such you must ensure that the
reverse proxies and load balancers utilized with Authelia are configured to remove and replace specific headers when
they come directly from clients and not from proxies in your trusted environment.
Some proxies require users explicitly configure the proxy to trust another proxy, however some implicitly trust all headers regardless of the source so you will have to manually configure them.
Network Rules
In particular this is important for Access Control Rules as the network criteria relies on the X-Forwarded-For header. This header is expected to have a true representation of the client’s actual IP address.
If this is not removed from non-trusted proxies a user could theoretically hijack any rule that contains this criteria to potentially skip an authentication criteria depending on how it is configured.
Cloud Proxies
In addition to configuring your own proxies to remove this header from untrusted sources, when using a cloud proxy like Cloudflare you must ensure they do this or you configure a rule to do it. We aim to have documentation in this section for cloud proxies that do this, but you should test this yourself and check the documentation for the cloud proxy.
In addition to this it’s important if you wish to preserve the clients actual IP address that you trust the IP addresses of the cloud proxy in your on-premise proxies. If you don’t do this most if not all proxies configured as per our guides will remove the header and everyone external will appear to come from a proxies source IP address rather than their real IP address in both logging and access control.
These same rules apply to any off-site hosted proxy or load balancing solution that alters the source IP address.
Cloudflare
Cloudflare adds the X-Forwarded-For header if it does not exist, and if it does exist it will just append another IP to it. This means a client can forge their remote IP address with the most widely accepted remote IP header out of the box.
It is therefore important you configure Cloudflare to remove this IP address. *Please Note: This is by no means an exhaustive guide on using Cloudflare transform rules, however it’s enough to configure a couple rules which should achieve a secure result. Please see the Cloudflare documentation on transform rules for more information._
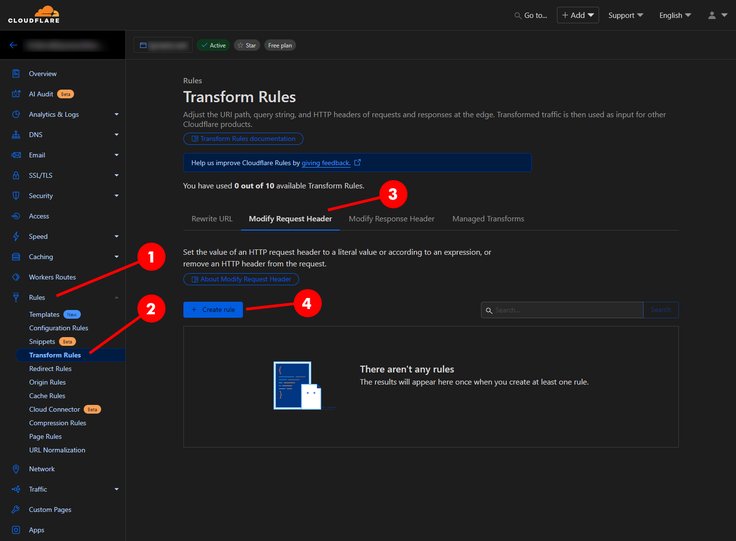
Steps
- On the left sidebar, click
Rules. - Click
Transform Rules. - On the right, click
Modify Request Headertab. - Click
Create rule. - Set the
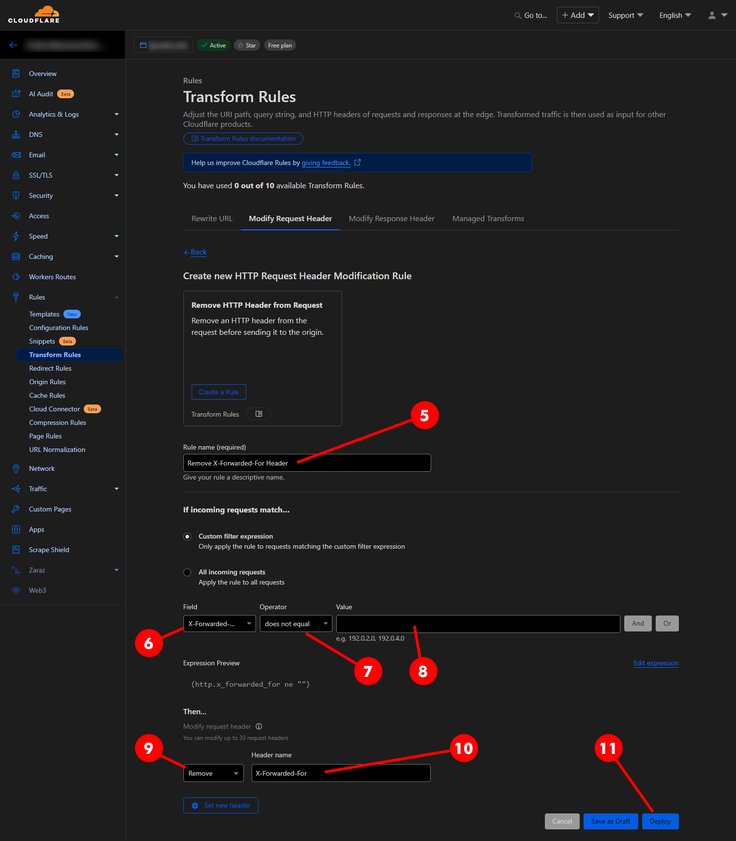
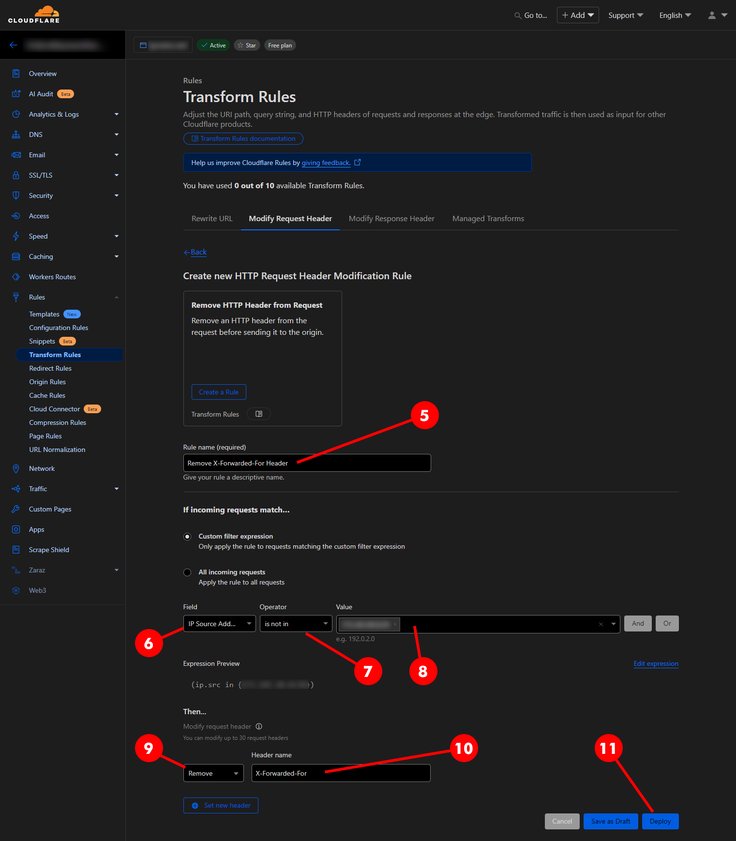
Rule nameto something appropriate likeRemove X-Forwarded-For Header. - Set the
Fieldoption in theWhen incoming requests matchsection to an appropriate value (see criteria table below). - Set the
Operatoroption in theWhen incoming requests matchsection to an appropriate value (see criteria table below). - Set the
Valueoption in theWhen incoming requests matchsection to an appropriate value (see criteria table below). - Set the
Thensection dropdown toRemove. - Set the
ThensectionHeader nametoX-Forwarded-For. - Click
Deploy.
Criteria
This table describes the criteria needed to achieve a desired result. Only one of these options should be chosen. You
Should look at the desired result column and apply the appropriate field, operator, and value to step 8.
Generally speaking the Always Remove option is the correct option.
| Desired Result | Field | Operator | Value |
|---|---|---|---|
| Always Remove | X-Forwarded-For | does not equal | blank |
| Remove When Not From Trusted Source | IP Source Address | is not in | list of trusted source addresses |
Cloudflare publishes its IP address ranges publicly at the easy to remember address https://www.cloudflare.com/ips/. You should use this with the trusted proxies section of your relevant proxy to ensure it’s trusted if you intend to use Cloudflare.